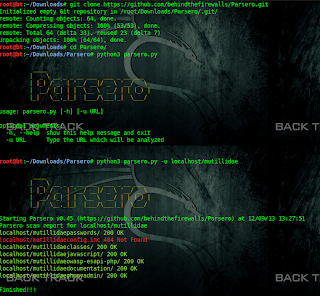
SOME COOL GOOGLE DORK
Symlink dork. Code: inurl:/sym/root/ & intext:"Parent Directory" c99shell dork. Code: inurl:(shell.php | c99.php) Encoder Bind Proc. FTP brute Sec. SQL PHP-code Feedback Self remove Logout c99shell dork(2). Code: inurl:(shell.php | c99.php) intitle:c99shell Encoder Bind Proc. FTP brute Sec. SQL PHP-code Feedback Self remove Logout WordPress MySQL details. Code: inurl:(wp-config.conf | wp-config.txt) ext:(conf | txt | config) Databases username && passwords. Code: inurl:/includes/ & ext:inc & inurl:connect | inurl:dbconnect & -site:phpkode.com Phish The Phisher Code: filetype:txt & intext:"email=" & intext:"pass=" & intext:"charset_test=" phpmyadmin exploit Code: allinurl:index.php?db=information_schema Here is list of other google dork. Download here .